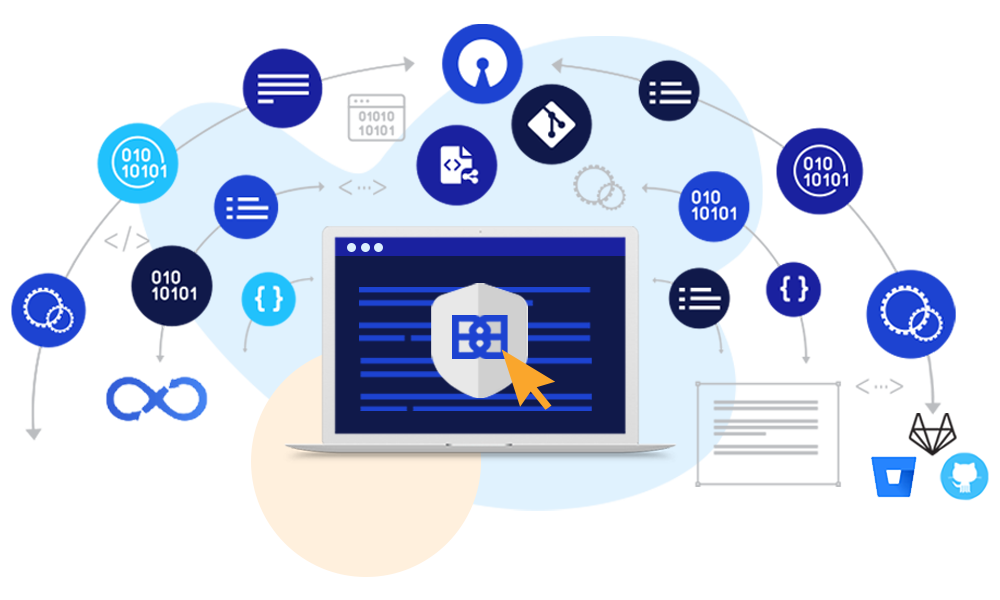
Secure your code.
Secure your software supply chain.
Attacks on the software supply chain are the largest threat facing security teams today.
BluBracket protects software supply chains by preventing, finding and fixing risks in source code, developer environments and pipelines so companies can ship secure code without sacrificing speed or innovation.
“Attackers are targeting software development systems, opensource artifacts and DevOps pipelines to compromise software supply chains.”
Gartner
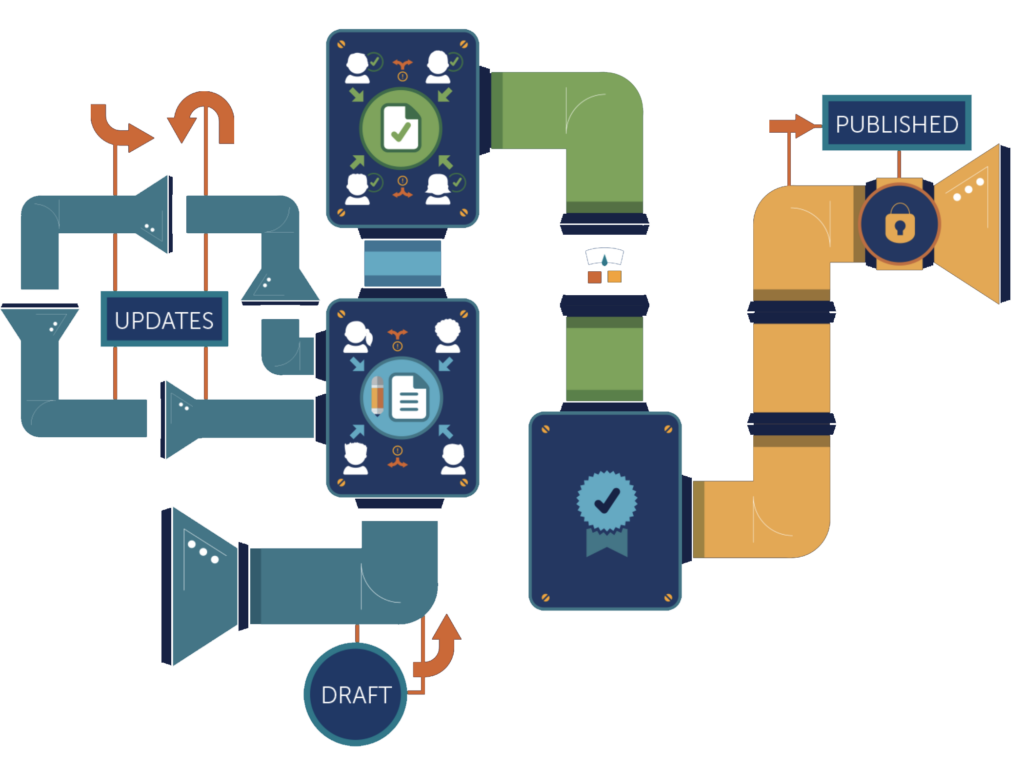
Code Security:
early, often and automated


Prevent secrets and credentials in code
Give developers the tools to keep secrets, PII and other credentials out of their code before it’s pushed–without slowing down their productivity.
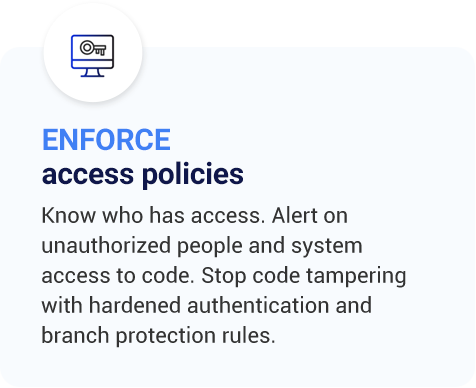
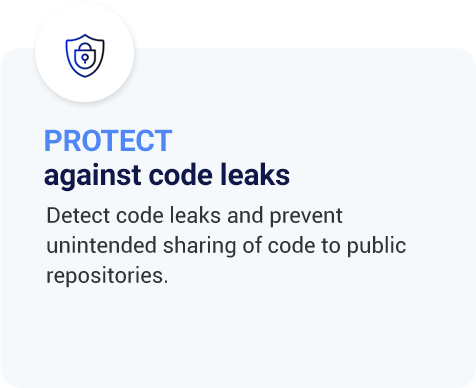
Detect code risks, credentials and misconfigurations
Continuously scan for code risks within and outside your enterprise to guard against code leaks, credentials in code or costly misconfigurations.

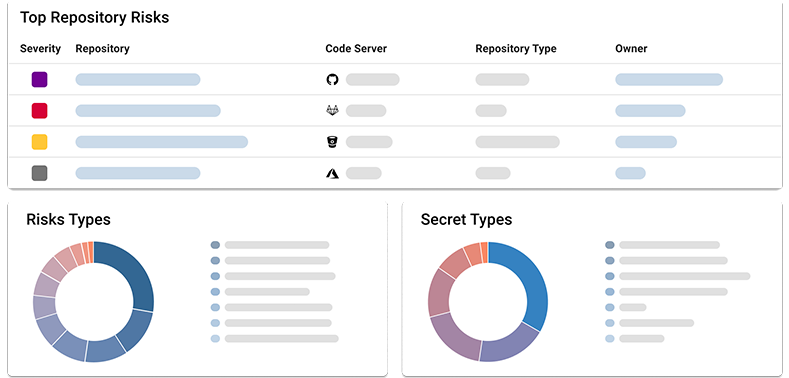
Prioritize the most critical risks from code
In a world of false positives and alert fatigue, get a Code Risk Score to instantly prioritize and fix the most critical risk from your code, development environments or pipelines.
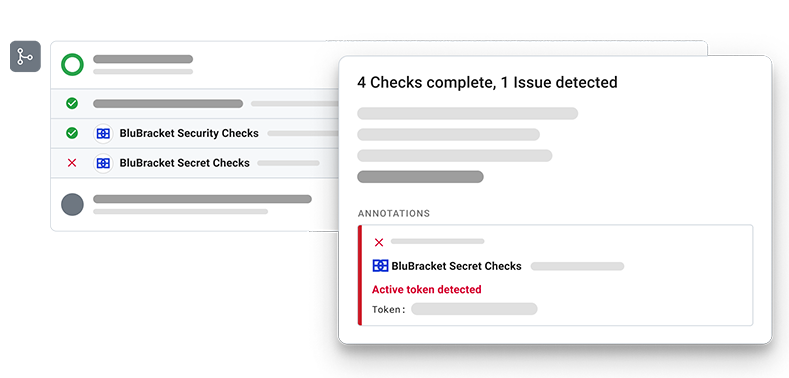
Remediate throughout your CICD pipelines and within Git
Fix issues from code throughout your CICD pipelines and across all major Git platforms to secure your internal software supply chain and bring developers and security together.
BluBracket integrates with
BluBracket scans the contributions of millions of developers to protect
$100B in annual revenue.
Innovative enterprises trust BluBracket

“At Priceline, our technology is a key differentiator. BluBracket provides a state of the art security solution for our code. By helping us catch security vulnerabilities in code early, this will enable us to innovate quickly and release safely.”
Martin BrodbeckCTO of Priceline 
“With BluBracket’s advanced secrets detection capabilities, seamless integrations, and source control governance features, we were able to rapidly advance our application security posture, providing value literally overnight. I don’t think a modern enterprise development program can afford not to have BluBracket.”
Andrew SchmittiHerb 
“BluBracket has an innovative solution to empower developers to keep sensitive information out of code before it’s committed to Git."
Jim ZemlinExecutive Director of the Linux Foundation 
"We’re excited to work with BluBracket on this important solution that protects our valuable IP and our systems."
John VisneskiData Protection Officer, The Pokemon Company International 
“Securing code is a key piece of our security puzzle, and it’s clear
BluBracket's vision delivers comprehensive security for the modern
software development cycle.”
Bill MartinerHead of Enterprise Technology at Compass Real Estate 
“Whether it’s infrastructure as code or the models that run our systematic trading strategies, code is in everything we do,” said John Terrill, Chief Information Security Officer at Point72. “BluBracket helps protect that code to keep our business innovating and our information safe.”
John TerrillCISO of Point72 Asset Management 
Previous
Next
Code Security Resource Center
See what’s new with BluBracket and code security.
- All
- Blog
- News
- Webinars
- White Papers